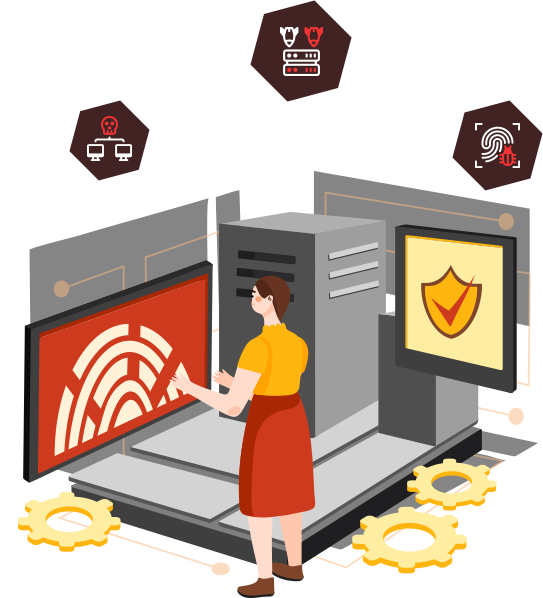
Secure Your Business From Cyber Threats
Rapid | Reliable | Affordable Security Solutions
We are dedicated to protecting our clients from the constantly evolving threats in the digital world.
virtual events
Cum sociis natoque penatibus et magnisd is parturient montes nasc.
August 11, 2021
new report
Cum sociis natoque penatibus et magnisd is parturient montes nasc.
August 11, 2021
expert panel
Cum sociis natoque penatibus et magnisd is parturient montes nasc.
August 11, 2021